Financial Services & Neo4j: Fraud Detection

Vice President, Product Marketing
5 min read

Identifying and stopping fraudulent activity is harder than ever for financial services organizations.
Standard anti-fraud technologies — such as a deviation from normal purchasing patterns — use discrete data. This is useful for catching individual criminals acting alone, but discrete methods fall short when it comes to detecting fraud rings. Furthermore, many discrete methods are prone to false positives, which can impact customer satisfaction and result in lost revenue.
Sophisticated criminals continuously alter their strategies to circumvent detection by traditional solutions. For example, they use synthetic accounts to carry out what appear to be unrelated activities, when in fact they are well coordinated.
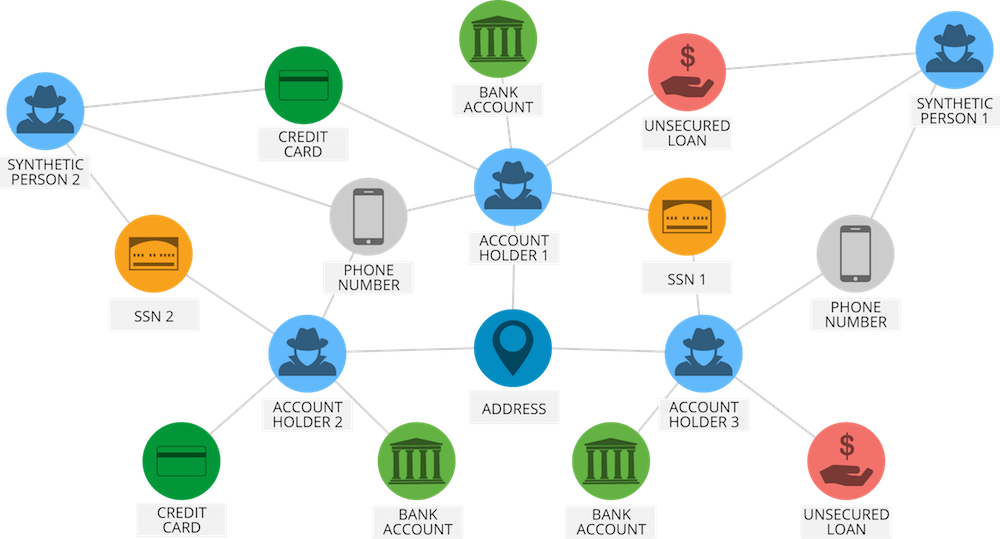
A criminal might steal identity information from ten different people. The criminal then mixes and matches the social security numbers, addresses, phone numbers and email addresses to create “new” synthetic identities that are then used to open bank and credit card accounts, as well as personal lines of credit.
Traditional fraud detection solutions won’t flag these accounts. Firms need a way to follow the trail from one account to another to determine how activities that on the surface appear unrelated are in fact connected.
In this series on Neo4j and financial services, we’ll be looking at how today’s finance enterprises are effectively solving emerging challenges in the industry. In previous weeks, we’ve taken a closer look at financial asset graphs, data lineage and metadata management.
This week, we’ll take a closer look at financial fraud detection.
Preventing and Detecting Financial Fraud
An increasing number of the world’s leading financial institutions are using Neo4j to model and monitor data about customers, accounts, devices, locations and other attributes to identify fraudulent activity from fraud rings using synthetic and stolen identities.
Uncovering rings with traditional relational database technologies requires modeling a graph as a set of tables and columns, and then carrying out a series of complex JOINs and self-JOINs. Such queries are very complex to build and expensive to run. Scaling them in a way that supports real-time access poses significant technical challenges, with performance deteriorating exponentially not only as the size of the ring increases, but also as the total dataset grows.
In contrast, graph databases are an ideal tool for overcoming these hurdles. Intuitive query languages like Cypher provide a simple semantic for detecting fraud rings in a graph, navigating connections in memory and in real time in order to catch the activity as it happens.
The graph data model below represents how the data actually looks to the graph database, and illustrates how one can find fraud rings by simply walking the graph.
Modeling a fraud ring as a graph
Augmenting one’s existing fraud detection infrastructure to support fraud ring detection can be done by running appropriate entity link analysis queries using a graph database, and running checks during key stages in the customer and account lifecycle, such as:
- At the time of account creation
- During an investigation
- When a credit balance threshold is hit
- When an overdraft occurs
Real-time graph traversals tied to the right kinds of events can help financial services firms identify probable fraud rings, during or even before a fraudulent transaction occurs.
Case Study: Fortune 500 Financial Services Company
A Fortune 500 financial services company conducts 2.2 million financial transactions per month. With the real-time graph analysis and simple data visualization provided by Neo4j, the company’s analysts stop millions in fraudulent transactions annually.
The majority of transactions processed by the financial services company are approved or denied through an automated fraud detection system. However, a portion of transactions is submitted to an analyst for manual review. Prior to Neo4j, analysts queried a Microsoft SQL Server database to evaluate the customer information as well as enriched data from outside vendors and data on related customers, such as potential members of a fraud ring.
Depending on the transaction request, queries could require four or more levels of traversals to extract and analyze the information. Queries were slow and returned complicated data that analysts had to review — all while the clock was ticking for customers waiting to transfer money. The company needed a more efficient way to analyze data.
This would require decreasing the amount of time needed to process fraud detection queries against the database and delivering simple data visualizations to analysts. In order to achieve real time results, the development team would need a database optimized for storing and traversing several levels of relationships.
Neo4j brought connected data into the company’s architecture in real time and provided data visualizations that allow analysts to make fast, accurate decisions. The graph revealed emerging clusters and relationships that had previously gone unnoticed which improved the accuracy of real-time fraud detection.
Each customer can now be represented by up to 30 nodes, each with up to 60 properties totaling over 216 million nodes and 680 million relationships in the total dataset.
With Neo4j’s simple data visualizations, it now takes an analyst about half the amount of time to manually review a requested financial transaction. This allows them to review nearly twice the number of transactions daily — stopping fraudulent transactions sooner and reducing wait times for non-fraudulent customers.
Conclusion
Enterprises with mature and growing fraud detection solutions not only avoid the expenses of fraud but also strengthen their position against less-prepared competition.
Sophisticated fraud rings are a complex and evolving threat to any financial services enterprise, and static solutions that rely on discrete data aren’t enough in order to overcome fraudulent activity. In order to sustainably stay ahead of fraudster’s emerging tactics, fraud detection teams need a solution that analyzes data connections and evolves to address new patterns of fraud.
When it comes to such connected data analysis, Neo4j is the best graph technology to handle the scale, performance and sophistication necessary to make a bottom-line difference for today’s leading financial services organizations.
In the coming weeks, we’ll take a closer look at other graph technology use cases within the financial services industry, including anti-money laundering, IT infrastructure monitoring, identity and access management, cybersecurity, and customer experience management.
Catch up with the rest of the financial services and Neo4j blog series: