The Future of the Intelligent Application: Granular Security

Vice President, Product Marketing
4 min read

Modern applications come with new requirements. Such applications incorporate
intelligence and learning. They require full context to support smart decision-making in
real time. These applications must be able to scale without limits to meet unexpected
demand. Furthermore, next-generation applications demand straightforward, robust
security and flexible architecture to comply with ever-increasing regulations.
Last week, in blog two of our four-part series on the future of the intelligent application, we looked at scalability, including sharding and federated graphs.
This week, we will discuss how Neo4j provides powerful robust, granular security.
Security
Neo4j Developers and administrators require granular control over access to data for security
and privacy.
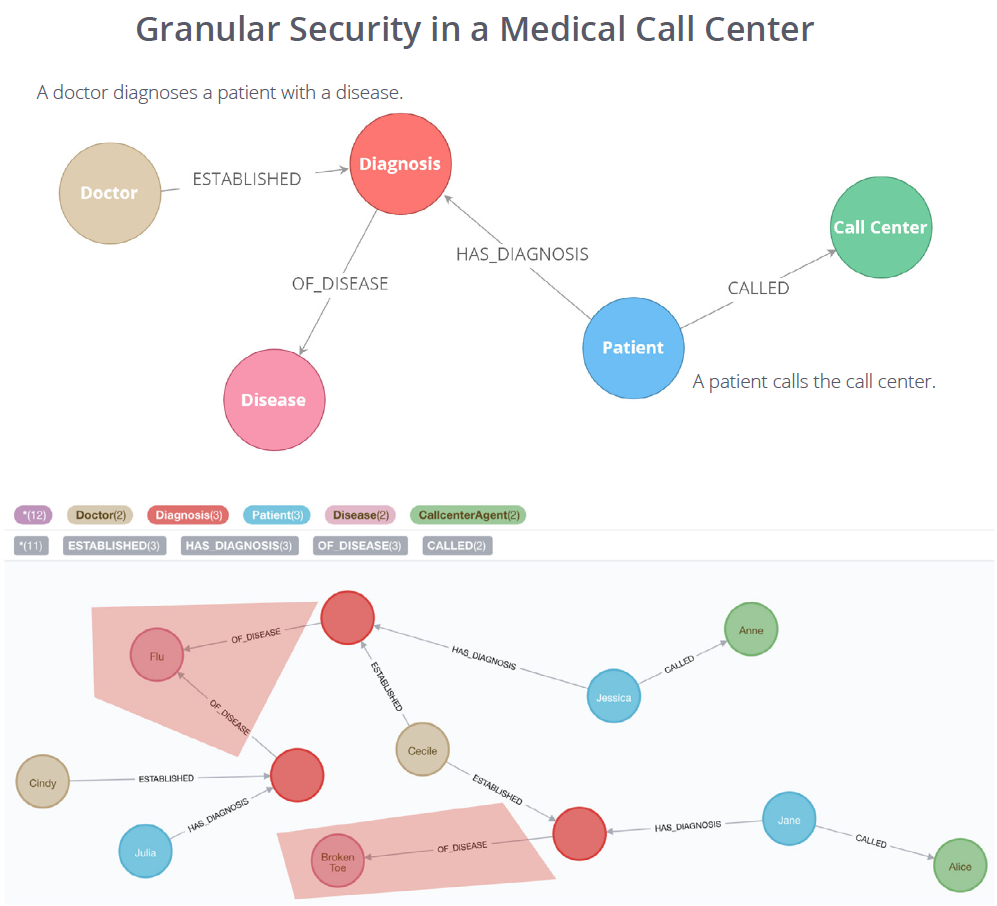
For example, a healthcare application can give doctors a view of a patient’s diagnosis while
an administrator only has access to the patient’s appointment schedule, ensuring that only the right users have access to the right data.
Robust data security is critical to the future of any database platform. Neo4j offers
granular security that provides role-based access control at the database level to support
the needs of different roles and applications.
Building security into the database simplifies secure application development. Rather
than tasking developers with backend security, developers write their applications against
a scalable and security-conscious backend. That backend is increasingly a database that
has both horizontal and vertical scale, as well as extremely fine-grained security controls.
As application development changes, today’s graph database needs to enforce rigorous
enterprise security rules while remaining easy to deploy and manage.
Neo4j offers identity and access control using Kerberos and LDAP. Communications with
the database take place over Neo4j’s internal binary protocol or using HTTPS requests.
Neo4j provides rule-based granular security that can be applied at the level of the data
model, as discussed next.
Granular Security
Security applied to a specific schema allows multiple users to have different views of the
same database. Each user is assigned a role, and that role has permissions to read – or
read and write – certain types of data.
In a graph data structure, this greatly simplifies the task of assigning permissions. For
example, with schema-based security you define the kind of access that a given user has
against a graph. One user may have access to all the objects, nodes and relationships.
Another user may have access only to some objects or some properties of given objects.
Granular security empowers security staff to create rules about sensitive data and know
that they will be applied at the database level. Administrators do not need to worry
about managing a complex distributed set of security capabilities; they declare specific
role-based permissions at the schema level and know that everything is protected in
accordance with those permissions. Granular security offers security configuration
consistency across Neo4j databases, clusters and shards.
Neo4j restricts what data is seen by different users, supporting role-based access control.
The restrictions are defined using database and schema information. Think of a human
resources database. With the right security rules in place, the same database serves as a
staff directory for everyone, as well as a database where sensitive HR information is kept.
Neo4j offers fine-grained security down to individual objects and their properties. Neo4j grants permission to traverse, read or write data based on node labels, relationship types or database and property names.
It defines and replicates security rules across the cluster using roles that are associated with users. These rules apply to everyone, even those who query the database using Cypher.
Consider a large research hospital connected with a university. Doctors, healthcare workers, researchers and administrative staff all have different security profiles. Doctors may have access to individual patient data but not billing information. Call center staff who schedule appointments need access to contact information for patients but not their diagnoses or other health information. Researchers gauging the impact of certain medications may have access to test results and selected demographic characteristics of a large group of patients but not to personally identifiable information.
Modern applications require embedded security that is applied no matter where data physically resides. Schema-based security offers this level of protection, regardless of whether there are multiple on-premise graph databases or an enormous graph sharded across multiple cloud repositories around the world.
A graph database may be sharded across hundreds of machines or clusters, but the schema describes all of the data in them. Organizations declare security rules based on that schema, and those rules are inherited by all users and applications that access the graph.
Conclusion
As we have shown in this third blog of our four-part series on the future of the intelligent application, Neo4j offers granular security at the schema level, providing an effective approach to governance and security for critical data.
Next week, in the final blog in this series, we will focus on how Neo4j supports business agility, making it easy to fluidly evolve your solution as business requirements change.
Today’s applications need a flexible, secure and scalable foundation – with prototypes in days, not months. Click below to get your copy of The Future of the Intelligent Application and learn why startups and enterprises alike build on Neo4j.