Computer security, cybersecurity or information technology security (IT security) is the protection of computer systems and networks from information disclosure, theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
Cybersecurity is also one of the significant challenges in the contemporary world, due to its complexity, both in terms of political usage and technology.
Graph database can help in implementing an effective solution in the field of Cyber Security.
Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win.
— John Lambert, Engineer from Microsoft Threat Intelligence Center
Our networks are connected graphs. We can use a graph based solution to have a holistic view of enterprise network.
This helps us to minimize the impact by:
- Quickly identify risks,
- Detecting anomalies, and
- Protecting our systems with confidence.
Example Use Case
With help of Dave Voutila, we came up with a very good example in the area of Cybersecurity. This demo is based on the data and themes from the BloodHound Project.
BloodHound: Six Degrees of Domain Admin – BloodHound 3.0.3 documentation
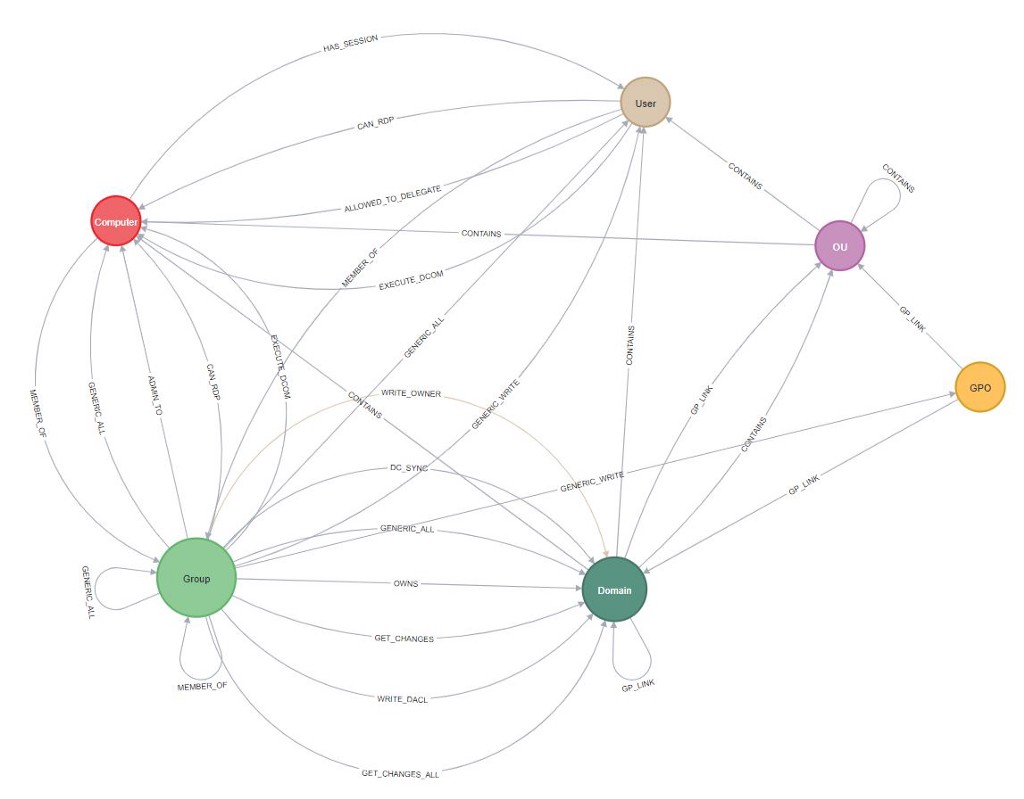
Bloodhound is a great tool for auditing your Active Directory environment. It uses Neo4j as a backing datastore and querying.
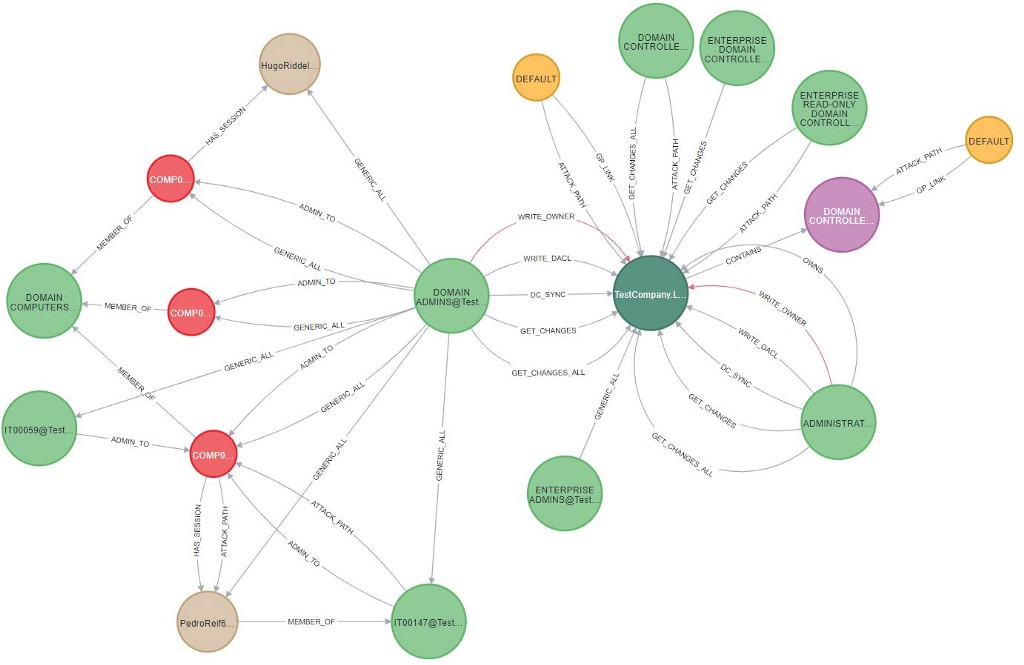
We have conceptualized a BloodHound example to prepare a fictitious Active Directory environment. Active Directory helps IT teams manage and monitor various network resources, machines and users. It allows to grant and revoke different permissions to users and groups.
Network Insights
In this example, we prepare the graph schema and load the Active Directory data in form of graph nodes and relationships. Further, we demonstrate some interesting queries to gain insights of the network assets and user access.
Attack Paths
Cybersecurity nowadays is seeing a zero trust (trust no one) shift of network defense. This approach allows organization to restrict access controls to network, apps and environment without sacrificing performance and user experience.
In a simple terms, we analyze any path that a user can take to reach to a high value resource in the network. Is this access (path) necessary? If not, these unwanted access paths can be revoked or controlled.
We have also demonstrated this aspect by showing all possible access paths leading to a network crown jewel (high value object in the Network), and possible attack paths.
Cybersecurity Dataset Available on AuraDB Free
The dataset and guide is available if you create a free AuraDB managed database. Just select the box for the dataset and give it a try.
Neo4j Sandbox to Explore Cybersecurity Example
We have a created a Neo4j Sandbox to walk you through the Cybersecurity use case. Neo4j Sandbox is a great — and free — online tool from Neo4j to try their graph database without installing anything locally.
Full source code for this example and guide is available on GitHub.
GitHub – neo4j-graph-examples/cybersecurity: Graphs in Cybersecurity – Bloodhound
Neo4j References
- Demo video Cyber Security
- Neo4j Bloom Persectives
- BloodHound Datacreator Library
- Neo4j for Cyber Security
External References
- BloodHound
- Bloodhound Handbook PDF
- Cyber Security- Wikipedia
- Hackerpocalypse Cybercrime Report-2016
- Cost of Cybercrime Study
- Forecast Analysis: Information Security, Worldwide
- Functional Post — John Lambert
Neo4j Cybersecurity AuraDB & Sandbox: Graphs for Cybersecurity was originally published in Neo4j Developer Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.




